Electronic Supply Chain Security
Folks, it's been a while since my last blog post. Almost a year I guess. Please accept my apologies. I've been somewhat busy with my university work and last few stages of CIMA. Today's post is an extract from a review paper I compiled sometime back as part of one of my university subjects. Hope you will find it useful. Be safe. Enjoy!
ELECTRONIC SUPPLY CHAIN SECURITY
Abstract: Supply
chain management is a ubiquitous topic that has evolved greatly over time. Developments
in technology added a new dimension and extended traditional supply chains to electronic
supply chains. Although this is a critical aspect of several global businesses
today, one major threat continuous to hinder the performance of e-supply
chains. Security is this dark cloud that looms over e-supply chains worldwide.
Index Terms:Electronic supply
chains, security
INTRODUCTION
Electronic
Supply Chain Management or E-Supply Chain Management is the buzzword among
global businesses today. In e-supply chain management, managing security risks
takes the top priority. Security risk is an inherent issue that comes along
with electronic channels. However the competitive nature of global markets has
meant that even a trivial mistake in security is intolerable. Therefore
overcoming this inherent issue is an essential requirement.
However,
companies continue to face severe security threats in their e-supply chains.
This study explores the security threats faced by companies, various kinds of
theoretical and practical solutions that already exist, limitations of existing
solutions and possible ways of overcoming the current issues.
I was motivated
to explore the buzz created by e-supply chain security issues using the network
security knowledge and supply chain management knowledge I have gathered
through my studies over the last few years as an undergraduate at Faculty of
Information Technology.
This
paper discusses the background of e-supply chains, research conducted in this
field, major security issues, common industry solutions and proposed solution.
BACKGROUND
I. Supply Chains and Supply
Chain Management
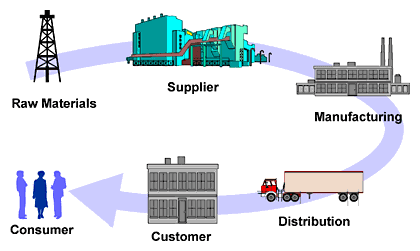
A supply
chain in simple terms can be described as a combination of value chains which
together provide the final product or service to the customers to satisfy their
needs and wants. A classic supply chain consists of suppliers, manufacturers,
wholesalers, retailers, end customers and other service providers.
Supply
chain management is a concept that involves the co-ordination of operations
from the supplier of raw materials at one end of the supply chain all the way
down to the consumer at the other end [7].
II. E-Supply Chains and
E-Supply Chain Management
A supply chain is called an e-supply
chain when it is electronically managed, typically with web-based software.
According to Williams, Esper, & Ozment (2002), e-supply chain management
refers to the management of a supply chain that is built via electronic
linkages and structurally based on technology-enabled relationships.
III. E-Supply Chain Security
E-supply chain information security can
be identified as soft security and hard security [5]. Hard aspect indicates
tangible vulnerabilities, such as physical thefts (facilities, equipment, and
personnel) or physical damages and terrorism. Soft aspect refers to intangible
vulnerabilities which in the above definition is considered as information
theft.
MAJOR RESEARCH IN E-SUPPLY CHAIN SECURITY
Supply chain management is an area that
has a great history behind it. But in early days, it was seen as a supporting
function by many organizations. In 1990s with the technology boom, electronic
supply chains became a strategic aspect of several organizations. Ever since
then, security has been the major concern where several theoretical models have
been introduced by researchers worldwide to overcome the security issues. Few
of them are summarized below.
I. e-Security Framework for
Supporting Efficient e-Supply Chain Management in Electronic Commerce
Environment by Sungmin Kang and Seng-Phil Hing, Korea Trade Research
Association [6]
This is a research conducted by the above
mentioned researchers in 2005 where they introduced a security framework and
architecture to deal with security concerns in e-supply chains and provide the
necessary support for supply chain process.
In this research, 2 main reasons were
identified as the triggers of security issues.
·
Network security
·
Increased
variety of products and decreased product life cycle
Security issues created due to these 2
main reasons were categorized into 10 different domains to suggest the security
framework and architecture for providing the optimal level of support for
business operations.
The e-security framework introduced by
Sungmin Kang and Seng-Phil Hing consists of 5 parts.
1.
Security
Strategy
2.
Security
mechanism
3.
Management
4.
Policy
5.
Technology
These 5 parts or layers could be applied
to e-supply chain management to provide solutions to the problems and issues
identified above.
II. Information Security Issues
in Global Supply Chain by Anand S. Kunnathur and Sridhar Vaithianathan [7]
The framework captures the main facets
that demand attention into 5 sections.
The most relevant section to this study, Emerging
Technologies Issues is further divided into 7 dimensions.
Although this model provides an effective way of identifying and classifying security issues in e-supply chains, the main limitation is that it does not provide ways to overcome these issues. That has been identified as a future research area by the authors of the study.
III. Electronic-Supply Chain
Information Security: A Framework for Information by Alizera Bolhari, Shahid
Beheshti University [2]
Alizera
Bolhari is an Iranian researcher who reviewed information security in e-supply
chains and proposed an e-supply chain information security framework.
Virus,
worm, Trojan horse, hacker, trap door, logic bomb, port scanning, spoof, DNS
attack, hoax, dumpster diving, sniffing, war dialing, and DoS attack were
identified as main information security threats to an e-supply chain.
Current
solutions such as passwords, firewalls, VPNs, digital signature, secure socket
layer (SSL), etc. are among the identified and reviewed existing solutions to
security issues.

INFORMATION
SECURITY THREATS
Business
organizations that operate a global or local e-supply chain are affected by several
security threats. Among all different types of threats, 4 common security
issues can be identified as follows.
I. Virus
Many
scientists have debated over the exact definition of a virus. But in simple
terms, virus is a computer program that leads to detrimental effects, such as
corrupting the systems or destroying data. It can be broken down into 3
functional areas called, replication, concealment and bomb [3].
·
Replication
A virus
hides in one legal file which can be macro, executable file or master boot
record. Once the infected file is executed or opened, the virus copies itself
to the computer and attach the copies to other original legal files in the
computer.
·
Concealment
A virus
conceals itself by hiding in fake code sections or polymorphic virus can mute
itself by changing its own code.
·
Bomb
Bomb
refers to a trigger where the virus can be configured to activate under certain
conditions. This condition can be a logical condition or a statement or a time
bomb where it will activate at a certain specified date and time.
Worms, Trojan
horses and logic bombs have fundamental technical differences to viruses.
However in terms of the objective and mode of operation, they have many
similarities to viruses.
II. Hacker
Hacking
in simple terms can be described as the act of gaining unauthorized access to a
computer. A hacker needs a deep understanding about computers and computer
networks [3]. There are 2 main types of hacking depending on the motivation or
the intent of the hacker.
White hat
hacking is where the hacker has a positive motive. This is commonly referred to
as ethical hacking as well. In white hat hacking, hacker might break into a
system and inform the owners about the vulnerabilities in the system. This can
be done either with or without the permission of the owners of the system. But
in any case, the intent of the hacker is not to exploit the system. In e-supply
chains, white hat hacking is not seen as a major theat. In fact, it has been a
common methodology used to identify vulnerabilities in e-supply chain systems.
Black hat
hacking is the flip side of white hat hacking where the hacker’s intent is
malicious. The hacker gains access to a system without the authorization of the
owners and exploits the system and information for his/her own advantage or on
request of a third party. This is seen as a major threat to e-supply chain
management.
III. Flooding
In
a network,
flooding is the forwarding by a router of
a packet from
any node to
every other node attached to the router except the node from which the packet
arrived. Flooding is a way to distribute routing information updates quickly to
every node in a large network.
However flooding
becomes a major issue when an excessive amount of unwanted data is sent [1].
This results in disruption of data availability. This is a common incident in
e-supply chains. Although it is deemed unethical, companies use flooding to
block the systems of other companies to obtain competitive advantage. This can
lead to significant delays which is detrimental in modern business
environment.
IV. DNS Attack
Domain Name
Service (DNS) attack refers to a manipulation of the domain name registry to
redirect a URL [4]. There are 3 main types of DNS attacks.
The first
type of DNS attack is called a cache poisoning attack. This can happen after an
attacker is successful in injecting malicious DNS data into the recursive DNS
servers that are operated by many ISPs. The second type of DNS attack happens
when attackers take over one or more authoritative DNS servers for a
domain. The third type of DNS attack is the most problematic to undo. It happens
when an attacker compromised the registration of the domain itself, and then
uses that access to alter the DNS servers assigned to it.
REVIEW OF EXISTING INDUSTRY SOLUTIONS
As
reviewed in the literature survey above, several researchers have proposed
various frameworks to overcome e-supply chain security issues. However in
reality, hardly any company uses these frameworks as they are considered to be
academic research and highly theoretical. Companies use a more flexible and
simple methodology which allows them to respond to security risks in a more
robust manner. Generally companies use 4 types of controls to overcome e-supply
chain security issues.
I. General Controls
General
controls refer to controls that apply to the entire e-supply chain system of
the company. This includes recruiting reliable and skilled employees, giving
appropriate training, supervision, segregation of duties, use of user IDs and
passwords, two-factor authentications and physical access controls such as
locks and back up storage.
II. Application Controls
These
controls refer to controls that apply to specific e-supply chain software
application. Specific applications can be supplier management systems,
inventory management systems, finance and accounting systems, sales and marketing
systems, labor and machine scheduling systems, customer relationship management
systems, etc.
III. Software Controls
The
argument behind software controls is that, if software applications are
original and purchased from an authorized and reputed seller, the risk created
by such software applications is minimal. But in practice, software piracy is a
common issue where companies use pirate versions due to their cheapness in
cost. However this not only exposes them to security threats, it also amounts
to breach of the law.
IV. Network Controls
This is
where companies have taken specific actions to overcome the risks created by
distributed or network computing. Some of the common network controls include
firewalls, data encryption, authorization, anti-virus software, etc.
When
analyzing these controls that are being used to overcome the security threats
created by e-supply chains, the main concern is that almost all of these
solutions are applied at the operational level of the organization. In a world
where e-supply chains are considered as a top notch strategic element, ideally
the security risks should also be handled at the strategic level especially
given its potential to destroy an entire company.
PROPOSED FRAMEWORK TO MANAGE E-SUPPLY CHAIN SECURITY
Everyone
believes that e-supply chain security matters should be handled at the
strategic level. Therefore firstly it is important to understand what is
actually meant by “handling at the strategic level”.
Every
company has a mission, vision, goals and objectives which eventually transpire
into the corporate strategy. Supply chain security matters should also be a
critical part of the corporate strategy handled by the top level employees of
the organization if it were to be called, “handled at the strategic level”.
Any
framework proposed should be simple, realistic and practical for it to be used
by businesses in the real world. Following steps can be used as a preliminary
guide to formulate the e-supply chain security strategy.
·
Appoint a
steering committee comprising of people representing different functions and
different management levels of the organization.
·
Conduct a situational
analysis to analyze the existing security issues faced by the company and the
other players in the industry.
·
Thorough study
of the corporate objectives and strategy of the organization.
·
Development of
objectives for the e-supply chain security strategy in line with the analyzed
corporate strategy and objectives.
·
Formulation of
the detail plan of action to overcome the identified security threats with the
participation of all the members.
·
Submission of
the formulated strategy (in the form of a report) to the board of directors and
obtaining their feedback.
·
Review and
refine the developed strategy based on the feedback received.
·
Implementation
of the strategy backed up by enterprise wide communication and education.
·
Monitoring and
controlling to ensure the strategy is implemented in practice.
DISCUSSION
E-supply
chain security is a main problem in global supply chains which needs to be
addressed quickly. Several research studies have proposed operational and
strategic frameworks to overcome the security issues. However the problem still
remains due to the complex and theoretical nature of the solutions provided
where companies in practice handle supply chain security issues at the
operational level. The suggested approach is a very simplistic yet a holistic,
flexible and practical way of handling e-supply chain security issues at the
strategic level.
This
review paper reviews e-supply chain and e-supply security, existing frameworks,
main security threats, current industry practices used to overcome the risks
and proposes a simple approach based on which e-supply chain security strategy
could be formulated.
REFERENCES
[1]
Bhaiji, Yusuf, (2008), Network Security Technologies and Solutions (CCIE
Professional Development Series), Cisco Press; 1 edition.
[2] Bolhari A (2009), Shahid
Beheshti University, Tehran, Iran, Electronic-Supply Chain Information
Security: A Framework for Information.
[3]
Brenton, Chris, Hunt, Cameron, (2001), Active Defense — A Comprehensive Guide to
Network Security, SYBEX Inc., CA.
[4]
Canavan, John E. (2001), Fundamentals of Network Security, Artech House
Publishers; 1st edition.
[5] Grainger A, (2007), Supply
Chain Security: Adding To a complex Operational and Institutional Environment.
[6] Kang S, Hong S P, (2005),
e-Security Framework for Supporting Efficient e-Supply Chain Management in
Electronic Commerce Environment.
[7] Kunnathur A S, Vaithianathan
S, (2008), Information Security Issues in Global Supply Chain.



Nice post
ReplyDeletesecurity services
Thanks for shearing about this I thinks its very hopeful post and very important post for us.I really appreciate sharing this great post. Keep up your work.Thanks for sharing this great article.Great information thanks a lot for the detailed article.
ReplyDelete전자부품판매
Cross-border shipments between Mexico and the U.S. can be a challenging and complex process. But our experienced staff can do it easily. So we can deliver customers parcel timely and safely. If you want to experience our service, come and visit us today. Supply chain management services mexico
ReplyDeleteWao, Amazing if you need to convert any file then use this;
ReplyDeleteFiles Converter Online
That has support various formats including those;
ReplyDeleteSwf to Jpeg
M4v to Jpg
3gp file to Jpeg
3gp to Mp3
3gp to Wav
This is an awesome post.Really very informative and creative contents. These concept is a good way to enhance the knowledge.I like it and help me to development very well.Thank you for this brief explanation and very nice information.Well, got a good knowledge.
ReplyDeleteDistribution Management System